Linux Du Command Examples
Posted: 2021-05-17 03:14:03 Source: https://linuxhint.com/linux-du-command-examples/
The Linux du command allows a user to quickly identify their disk usage information. The Du command also help to view disk information usage in different formats. In this article, we are going to discuss the different uses and functions of the du command and provide examples for each function.
How to Install Ventoy on Ubuntu
Posted: 2021-05-17 02:08:34 Source: https://linoxide.com/how-to-install-ventoy-on-ubuntu/
How to Use Multiple Delimiters in AWK
Posted: 2021-05-17 01:50:49 Source: https://linuxhint.com/use-multiple-delimeters-in-awk/
This article provides an easy step-by-step guide on how to use multiple delimiters in the AWK programming language. The instructions include an explanation of AWK and its benefits, the definition of the delimiters, and a sample case to show how to separate the multiple delimiters using the AWK Field Separator.
How to Modify a Host File in Linux
Posted: 2021-05-17 01:31:44 Source: https://linuxhint.com/modify-etc-host-file-linux/
This article provides an easy step-by-step guide on how to modify a Host File in Linux. The instructions include how the host files work, how to edit the Linux host files, how to add domains and the corresponding IP into the host files, and create invalid domains to block websites.
How to Create a View in MySQL
Posted: 2021-05-17 01:24:57 Source: https://linuxhint.com/create-view-mysql/
In MySQL, a view is a virtual table that does not store data but shows data stored in other tables. Views are nothing but SQL queries because they store SQL queries that return a result set. They are also known as virtual tables. How to Create a View in MySQL is explained in this article.
How to Debug SSH Connections
Posted: 2021-05-17 00:44:29 Source: https://linuxhint.com/debug-ssh-connections/
A common cause of SSH connection errors is the service not running on the remote host. This can be because of accidental service shutdown or service not starting after a system reboot. In this article, some major causes of SSH connection errors and how to resolve them is explained.
How and When to Use MySQL UUID Type
Posted: 2021-05-17 00:26:44 Source: https://linuxhint.com/use-mysql-uuid-type/
Universal Unique Identifier, known as UUID, is a 128-bit long value that is unique across the globe. UUID values are incredibly fascinating because even if the values are generated from the same device, they can never be the same. How and When to Use MySQL UUID Type is explained in this article.
DistroWatch Weekly, Issue 917
Posted: 2021-05-17 00:18:02 Source: http://distrowatch.com/11245
This week in DistroWatch Weekly: Review: Fedora 34News: Haiku developing RISC-V port, NetBSD getting polished audio mixer, Fedora dropping remote root password authentication from installer, Vine Linux changes release cycleQuestions and answers: Providing a distro mirrorReleased last week: Bodhi Linux 6.0.0, NomadBSD 130R-20210508, UBports 16.04 OTA-17Torrent corner: ArcoLinux,....
5.13-rc2: mainline
Posted: 2021-05-16 22:27:44 Source: http://www.kernel.org/
| Version: | 5.13-rc2 (mainline) |
|---|---|
| Released: | 2021-05-16 |
| Source: | linux-5.13-rc2.tar.gz |
| Patch: | full (incremental) |
How to Enable Screen Sharing on Debian 10
Posted: 2021-05-16 09:38:13 Source: https://linuxhint.com/enable-screen-sharing-debian-10/
VNC or Virtual Network Computing is a protocol used to access the graphical desktop environment of your computer and control it from a remote computer. The Screen Sharing feature of the GNOME 3 desktop environment uses the VNC protocol to allow remote access to the GNOME 3 desktop environment of your computer. How to Enable Screen Sharing on Debian 10 is explained in this article.
The Difference Between a Real User ID and an Effective User ID in the Linux OS
Posted: 2021-05-16 06:31:18 Source: https://linuxhint.com/difference-between-real-effective-user-id-in-linux-os/
This comprehensive article provides the main difference between a Real User ID and an Effective User ID in the Linux Operating System. It highlights the advantages, disadvantages, restrictions, and capabilities of each User ID. The easy-to-follow commands are included to determine the scope of permitted activities for each User ID.
Linux cp Command Examples
Posted: 2021-05-16 06:28:24 Source: https://linuxhint.com/cp-command-linux/
Copying files and directories is an important task that is performed daily. All users need simple and easy utility through which they can copy all their files and directories. For this purpose, the most common cp command-line utility is used on UNIX and Linux systems. In this article, Linux cp command is explained with examples.
Linux “ls” Command Examples
Posted: 2021-05-16 06:27:22 Source: https://linuxhint.com/linux-ls-command-examples/
“ls” is one of the most frequently used commands in Linux. It is used to list down the files and sub-directories within your current directory. This command is equally useful for normal users as well as for system administrators. In this article, Linux “ls” command is explained with examples.
LVM: How to Create Logical Volumes and Filesystems
Posted: 2021-05-16 06:23:36 Source: https://linuxhint.com/lvm-how-to-create-logical-volumes-and-filesystems/
Logical Volume Management, or LVM, is a system used to manage logical volumes and filesystems. LVM has much more advanced features than the other volume management tools used to divide a disk into one or more partitions. Some files need to be stored in one filesystem and some files in another depending upon the requirement. How to Create Logical Volumes and Filesystems is explained in this article.
Selenium Automating Web Browsers
Posted: 2021-05-16 06:22:24 Source: https://linuxhint.com/selenium-automating-web-browsers/
Selenium is a very powerful tool to do very many things. Selenium is used to automate boring tasks; it automates browsers. From navigating the web to automatically logging into accounts to creating bots for various tasks can be achieved using Selenium. Selenium Automating Web Browser is discussed in this article.
House Price Prediction Using Linear Regression
Posted: 2021-05-15 17:53:22 Source: https://linuxhint.com/house-price-prediction-linear-regression/
Linear Regression is a supervised machine learning model that attempts to model a linear relationship between dependent variables (Y) and independent variables (X). It is used to predict the values in a continuous range instead of classifying the values in the categories. Linear regression is used for performing different tasks like house price prediction. In this article, every factor to perform the house price prediction in linear regression is explained.
Best Graphical Version Control Apps for Linux
Posted: 2021-05-15 17:43:22 Source: https://linuxhint.com/graphical-version-control-apps-linux/
The article list all the useful graphical dedicated version control apps for Linux though not may graphical clients are available as command line usage in more prevalent on Linux.
Systemd Service Hardening
Posted: 2021-05-14 16:00:00 Source: https://www.linuxjournal.com/content/systemd-service-strengthening

Introduction
In an age where hacker attacks are a daily occurrence, it is of fundamental importance to minimize the attack surface. Containerization is probably the best way to isolate a service provided for the public, but this is not always possible for several reasons. For example, think of a legacy system application developed on systemd. This could make the most of the capabilities provided by a systemd-based operative system and it could be managed via a systemd unit, or it could automatically pull updates using a systemd timer, and so on.
For this reason, we are going to explain how to improve the security of a systemd service. But first, we need to step back for a moment. With the latest releases systemd has implemented some interesting features relating to security, especially sandboxing. In this article we are going to show step-by-step how to strengthen services using specific directives, and how to check them with the provided systemd suite.
Debugging
Systemd provided an interesting tool named systemd-analyze. This command analyzes the security and the sandboxing settings of one or more specified services. The command checks for various security-related service settings, assigning each a numeric "exposure level" value, depending on how important the setting is. It then calculates an overall exposure level for the whole unit through an estimation in the range 0.0…10.0, which tells us how exposed a service is security-wise.
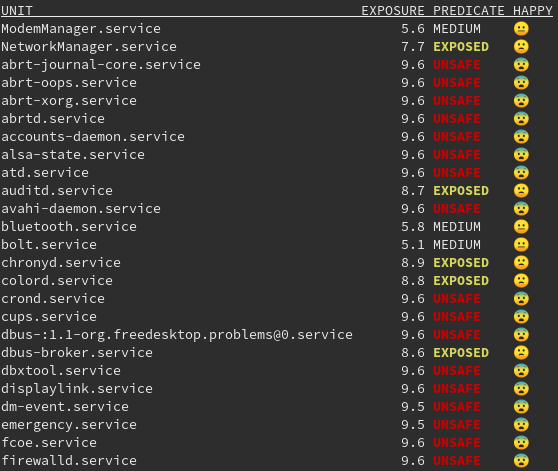
This allows us to check the improvements applied to our systemd service step-by-step. As you can see, several services are now marked as UNSAFE, this is probably due to the fact that not all of the applications are applying the features provided by systemd.
Getting Started
Let's start from a basic example. We want to create a systemd unit to start the command python3 -m http.server as a service:
[Unit] Description=Simple Http Server Documentation=https://docs.python.org/3/library/http.server.html [Service] Type=simple ExecStart=/usr/bin/python3 -m http.server ExecStop=/bin/kill -9 $MAINPID [Install] WantedBy=multi-user.target
Save the file and place it under the specific systemd directory of yor distribution.
By checking the security exposure through systemd-analyze security we get the following result:
How to install Ubuntu MATE 21.04
Posted: 2021-05-14 15:11:17 Source: https://www.youtube.com/watch?v=vEc404M37YI
How to use git reset
Posted: 2021-05-14 09:15:05 Source: https://linuxhint.com/use-git-reset-command/
Sometimes, the git users need to undo the changes done in the repository for the project purpose. `git reset` command is used to do this task. Different types of reset mode options can be used with this command. How to use git reset command is explained in this article.